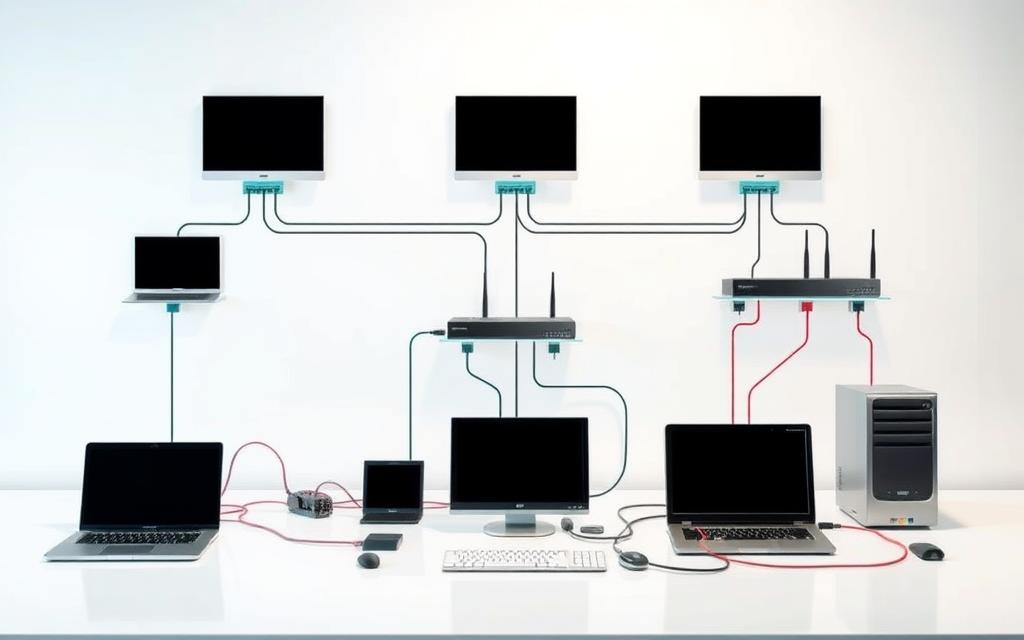
Understanding Computer Networks: A Beginner’s Guide
Modern life runs on computer networks. These systems link devices like smartphones, laptops, and servers to share data and resources. From streaming movies to collaborating on Google Drive, networks power daily activities seamlessly.
The concept dates back to ARPANET, a 1960s U.S. Defense project that pioneered packet switching. Today’s networks use advanced protocols like TCP/IP to manage communication across four structured layers. Wireless technologies such as Wi-Fi (IEEE 802.11) eliminate cable clutter while maintaining speed.
Industries from healthcare to finance rely on these connections. Networks enable real-time transactions, remote diagnostics, and cloud storage. Emerging innovations like 5G and IoT are expanding possibilities further.
This guide explores fundamental components: nodes, links, and security measures. You’ll learn how devices interact through standardized rules to create functional area networks. Master these basics to navigate our increasingly connected world.
What Does Computer Network Mean?
Global connectivity began with a 1969 Department of Defense project and now spans billions of computing devices. A network formally links two or more systems via cables or wireless signals to share data. Early models like ARPANET used room-sized mainframes, while today’s ecosystems integrate smart refrigerators and traffic sensors.
- Endpoints: Phones, servers, or printers that send/receive information
- Connections: Fiber optics for speed or Wi-Fi for mobility
- Protocols: Rules like TCP/IP that standardize communication
Architectures vary by purpose. Client-server models centralize resources (e.g., email platforms), while peer-to-peer networks enable direct file sharing. Enterprises use VPNs to securely link offices, whereas homes rely on routers for streaming and browsing.
The internet operates on practical TCP/IP stacks, though the OSI model’s seven layers guide theoretical design. With sensitive data flowing through networks, encryption and access controls are critical. Tools like Google Drive exemplify real-time collaboration powered by these systems.
Standardization bodies like IEEE and ISO ensure interoperability across devices. From the late 1960s to today, networks have transformed from military tools to societal necessities.
Key Components of a Computer Network
Every efficient system relies on core elements working together. In digital ecosystems, specific hardware, connections, and rules enable seamless operations. These components form the backbone of modern connectivity.

Network Devices: Nodes and Hardware
Physical equipment powers data exchange across systems. Essential network devices include:
- Routers (Cisco, Juniper): Direct traffic between different networks
- Switches: Connect multiple nodes within a local system
- Servers (AWS EC2): Host applications and store critical data
Endpoints like smartphones and IoT sensors also serve as access points. Enterprise setups often deploy firewalls (Palo Alto) for protection.
Links: Wired vs. Wireless Connections
Transmission media come in two primary forms:
- Wired: Cat 6A Ethernet (10 Gbps) and OM4 fiber (100G SR4)
- Wireless: Wi-Fi 6E (6GHz band) and Bluetooth 5.3
Fiber optics offer blistering 400 Gbit/s speeds for data centers. Power over Ethernet (PoE++) simplifies IoT device deployment.
Communication Protocols: Rules of Data Exchange
Standardized communication protocols ensure devices understand each other:
- HTTP/3 over QUIC for faster web browsing
- TLS 1.3 for encrypted data transfers
- SD-WAN solutions (Silver Peak) for optimized traffic
These digital languages govern everything from email delivery to video streaming.
Network Defense: Security Essentials
Protection measures have evolved with increasing threats:
- Next-gen firewalls (FortiGate) with deep packet inspection
- Zero Trust frameworks requiring continuous authentication
- Quantum-resistant encryption preparations
Storage Area Networks (Dell EMC PowerStore) implement additional access controls. Regular updates and monitoring complete the security posture.
The Evolution of Computer Networks
Digital connectivity has transformed dramatically since its military origins. The 1950s SAGE system, developed for the Department of Defense, marked the first computer-aided air defense network. This Cold War project used telephone lines to link radar stations.
Breakthroughs accelerated in the late 1960s with ARPANET. Funded by military research, this system pioneered packet switching—the foundation of today’s internet. By 1973, Xerox PARC engineers filed patents for Ethernet, enabling local data transmission.
Key milestones reshaped networking:
- 1983: TCP/IP became standard protocols, replacing older NCP systems
- 1991: Tim Berners-Lee’s WWW invention democratized information access
- 2007: Smartphones forced mobile optimization of networks
Speed advancements tell their own story. The 1958 Bell 101 modem managed 110 bit/s. Contrast this with 2023 fiber optics handling 800G transmission rates—a 7-billion-fold increase.
Modern innovations continue this trajectory:
- Wi-Fi 6/7 delivers multi-gigabit wireless speeds
- Software-defined networking (SDN) replaced rigid hardware configurations
- AI-powered security operations centers monitor threats in real-time
From room-sized mainframes to cloud architectures, networks keep evolving. Each leap forward builds on previous breakthroughs, creating faster and more secure connections.
Types of Computer Networks
Digital infrastructures vary in scale and purpose, each designed for specific connectivity needs. Businesses and individuals use different configurations depending on speed requirements, geographic coverage, and security protocols. Understanding these variations helps optimize performance for tasks from file sharing to global cloud access.

Local Area Network (LAN) and Wide Area Network (WAN)
Local area networks serve confined spaces like offices or campuses. These high-speed systems deliver data at 1-100 Gbps using Ethernet or Wi-Fi 6. Common setups include:
- Cisco Meraki setups for smart office buildings
- Industrial Ethernet for manufacturing robots
- Gaming LAN parties with low-latency connections
In contrast, wide area networks connect distant locations. AT&T’s MPLS services and VMware’s SD-WAN solutions enable secure cross-country links. AWS Global Accelerator demonstrates global WAN capabilities with anycast IP routing.
Specialized Networks: SAN, PAN, and VPN
Storage Area Networks (SAN) use Fibre Channel or iSCSI protocols for high-speed data access. Modern configurations leverage NVMe-oF for flash storage performance. Healthcare facilities deploy wireless PANs (MBANs) to monitor patient vitals through wearable devices.
Virtual Private Networks (VPNs) create secure tunnels across public infrastructure. Enterprises choose between:
- Cisco AnyConnect for IPsec encryption
- OpenVPN SSL solutions for remote teams
- WireGuard for lightweight mobile access
Cloud and Hybrid Networks
Microsoft Azure Virtual WAN architecture simplifies global cloud connectivity. Hybrid solutions like AWS Outposts extend cloud capabilities to on-premises data centers. Emerging 5G network slicing enables dedicated enterprise WAN channels with guaranteed latency.
IoT deployments increasingly adopt LoRaWAN for low-power sensors, while NB-IoT provides cellular coverage. China’s Micius satellite demonstrates quantum networking potential with hack-proof data transmission.
How Computer Networks Work
Data flows through networks like highways, following strict digital rules. Every email, video call, and file transfer breaks into standardized packets before transmission. These digital containers ensure reliable delivery across diverse devices and connections.

- Header: Source/destination IP address (like a mailing label)
- Payload: Actual content being transmitted
- Trailer: Error-checking data (CRC checksum)
Ethernet networks typically handle 1,500-byte packets, while data centers use 9,000-byte jumbo frames. The Border Gateway Protocol (BGP) maintains internet routing tables, directing traffic across 70,000+ network paths globally.
Data encapsulation transforms information through layers:
- Application data wraps in TCP/UDP headers
- IP addressing information gets added
- Physical layer converts everything to bits
Address Resolution Protocol (ARP) bridges logical IP addresses to physical MAC identifiers. Home routers use Network Address Translation (NAT) to share single public IPs among multiple devices—a process happening in your Wi-Fi right now.
Quality of Service (QoS) mechanisms prioritize critical communication like VoIP calls. DSCP markings in packet headers ensure smooth video conferences even during heavy downloads. Cloudflare’s CDN architecture demonstrates this by caching content at 300+ edge locations worldwide.
Advanced techniques optimize performance:
- VMware NSX micro-segmentation enhances security
- Round-robin load balancing distributes server requests
- Forward error correction compensates for packet loss
Industrial systems now implement time-sensitive networking for precise machine coordination. Optical Transport Networks (OTN) form the backbone with defined hierarchy layers—electrical, optical, and service.
Common Network Topologies
The blueprint of digital connectivity lies in its underlying structures. Different network arrangements optimize for speed, redundancy, or cost efficiency. Enterprises choose topologies based on data flow needs and security requirements.
Centralized and Sequential Designs
Star topology dominates modern setups with centralized switches. Data centers use leaf-spine architecture for scalable connections. This design isolates failures but depends on core devices.
Ring networks like FDDI create closed loops for traffic. Nodes pass tokens clockwise, preventing collisions. Financial systems adopted this for predictable latency.
Legacy bus systems used coaxial cables (10BASE2). While obsolete, they influenced early Ethernet protocols. Today’s variants appear in automotive CAN buses.
Redundant and Hierarchical Models
Full mesh links all devices directly, achieving <1ms latency. Stock exchanges use this for real-time trading. Partial mesh balances cost and redundancy in carrier backbones.
Tree topology mirrors organizational charts with root routers. Cable providers deploy hybrid fiber-coaxial (HFC) systems this way. It simplifies troubleshooting through segmentation.
Emerging designs include:
- Software-defined topologies that adapt to data demands
- Blockchain networks with decentralized peer connections
- MANETs for military field communications
Communication Protocols in Networking
Digital conversations rely on structured rules to ensure seamless interactions. Communication protocols act as the grammar of data exchange, governing how devices connect and share information. These standardized rules enable everything from email delivery to real-time video calls.
TCP/IP Model Layers
The TCP/IP stack powers modern internet connectivity through four functional layers:
| Layer | Function | Key Protocols |
|---|---|---|
| Application | User-facing services | HTTP/3, DNS, SMTP |
| Transport | End-to-end connections | TCP (reliable), UDP (fast) |
| Internet | Logical addressing | IPv6, ICMP |
| Network Access | Physical transmission | Ethernet, Wi-Fi |
TCP window scaling enables high-speed transmission by dynamically adjusting data flow. HTTP/3 over QUIC reduces latency by eliminating head-of-line blocking. These innovations demonstrate protocol evolution.
Ethernet and Wireless Standards
Wired and wireless technologies follow distinct protocols for optimal performance:
- Ethernet evolution: 10BASE-T (10 Mbps) to 800GBASE-R (800 Gbps)
- Wi-Fi 7 features: 320 MHz channels and 16 spatial streams
- Industrial systems: PROFINET for factory automation
Emerging standards address specialized needs:
- Time-sensitive networking (IEEE 802.1Qbv) for industrial IoT
- 5G NR protocols supporting massive machine-type communications
- Matter smart home standard over Thread mesh networks
Quantum key distribution introduces unhackable security through photon-based encryption. These advancements showcase how protocols adapt to new technological frontiers.
Benefits of Using Computer Networks
Organizations leverage connected systems to drive efficiency and innovation. Shared resources across devices reduce operational costs while improving productivity. Modern network infrastructures deliver measurable advantages for businesses of all sizes.
Cost savings lead the advantages with 73% hardware reduction through virtualization. AWS demonstrates this with petabyte-scale architectures that grow with demand. Enterprises eliminate:
- Redundant storage purchases
- Underutilized server capacity
- Excessive energy consumption
Real-time collaboration transforms workflows. Microsoft Teams direct routing integrates with existing phone systems. Centralized security through Azure Active Directory simplifies access control for distributed teams.
High availability architectures ensure business continuity:
- Kubernetes clusters automate failover
- SAN replication protects critical data
- AWS Outposts reduce edge computing latency
Emerging technologies push boundaries further. Juniper Mist applies AI to optimize WiFi performance automatically. Energy Efficient Ethernet cuts power usage by up to 80% during low network activity.
Compliance becomes manageable through HIPAA-aligned segmentation. Automated provisioning with Ansible modules accelerates deployment. These advantages create resilient, future-ready organizations.
Unified communication platforms like Cisco Webex demonstrate the convergence of benefits. They combine secure access, centralized management, and real-time data flows into single solutions.
Network Security Best Practices
Protecting digital assets requires robust security strategies. With cyber threats growing more sophisticated, organizations must implement multi-layered defenses. These measures safeguard sensitive data while maintaining network availability for legitimate users.
Firewalls and Encryption
Next-generation firewalls analyze traffic using machine learning. Palo Alto’s ML-powered solutions detect zero-day threats by comparing behavior patterns. These systems block malicious payloads before they reach internal devices.
End-to-end encryption ensures data confidentiality during transmission. The Signal protocol provides military-grade protection for communications. TLS 1.3 has become the standard for securing web access and API connections.
Microsegmentation divides the network into secure zones. Cisco’s SD-Access implements policy-based access controls at the device level. This approach limits lateral movement if breaches occur.
Quantum-resistant cryptography prepares systems for future threats. NIST-approved algorithms like CRYSTALS-Kyber will protect against quantum computing attacks. AWS CloudHSM offers FIPS 140-2 Level 3 validated hardware modules.
Preventing Insider Threats
Insider incidents cost enterprises $15 million on average in 2023. Darktrace’s UEBA solutions monitor employee behavior for anomalies. AI detects unusual data transfers or after-hours access attempts.
Least-privilege principles restrict users to essential resources only. Zscaler Private Access enforces this through SASE architecture. Continuous authentication in Zero Trust models verifies identities repeatedly.
Air-gapped backups mitigate ransomware damage. These isolated copies prevent encryption by malware. Regular drills test restoration procedures for critical devices and databases.
DNSSEC validation prevents DNS spoofing attacks. Combined with centralized management tools, it creates comprehensive protection. Employee training completes the strategy by reducing human error risks.
Effective security blends advanced technology with vigilant processes. Regular audits and updates ensure defenses evolve with emerging threats. These practices create resilient infrastructures that support business growth.
Objectives of Deploying a Network
Strategic network deployment unlocks operational efficiencies across industries. Organizations achieve 45% latency reductions through edge computing while NVMe-oF storage delivers 10 million IOPS. These systems transform how businesses share resources and process critical data.
- Cost optimization: Azure Arc hybrid models reduce hardware expenses by 73%
- Real-time access: Arista 7130 switches enable 400ns trading latency
- Scalable management: Google Anthos simplifies multi-cloud system control
Industry-specific solutions demonstrate versatility:
- Healthcare: GE CARESCAPE monitors patient vitals via medical IoT
- Smart cities: Cisco Kinetic platforms analyze traffic patterns
- Warehousing: Private 5G networks automate inventory robots
Modern architectures support emerging needs. LoRaWAN protocols connect thousands of sensors per gateway. AI training clusters like NVIDIA Quantum-2 accelerate model development. These capabilities ensure security and reliability for distributed users.
Content delivery networks (Akamai Edge) and remote work tools (Citrix SD-WAN) complete the ecosystem. Each deployment aligns network resources with business goals—from revenue growth to regulatory compliance.
Enterprise vs. Home Networks
Businesses and households rely on different network setups for distinct needs. Corporate environments demand industrial-grade infrastructure, while residential spaces prioritize simplicity.
Scale differs dramatically. Campus networks span multiple buildings with fiber optic backbones. Smart homes typically use a single router managing 25+ devices.
Security implementations contrast sharply:
- Enterprises: Deploy Cisco ISE for role-based access control
- Homes: Rely on WPA3 encryption in consumer routers
Traffic prioritization varies by use case. VoIP gets guaranteed bandwidth in offices. Residential networks rarely implement QoS beyond basic bandwidth limits.
Management tools reflect complexity differences:
- SolarWinds monitors enterprise-wide systems
- ASUS mobile apps handle basic home router settings
Storage solutions adapt to data volumes. SANs serve high-performance enterprise needs, while NAS boxes suffice for family photo backups.
Emerging trends show divergence:
- Businesses adopt 25G Ethernet for data centers
- Homes gradually upgrade to multi-gigabit Wi-Fi 6
Both environments continue evolving, but with fundamentally different technical and budgetary constraints.
Future Trends in Networking
The next decade will witness radical transformations in digital infrastructure. Breakthroughs from terahertz frequencies to brain-inspired chips will redefine connectivity standards. These advancements address growing demands for speed, security, and intelligent network management.
Speed milestones dominate the roadmap:
- 6G development targets 1 Tbps speeds using terahertz bands by 2030
- Starlink’s laser links achieve 100Gbps for orbital data relays
- Neuromorphic processors enable sub-millisecond routing decisions
Quantum innovations enhance protection. China’s 1,200km quantum satellite tests demonstrate hack-proof communication. NIST-approved post-quantum protocols will replace vulnerable encryption by 2025. Enterprises like AWS already offer quantum-resistant key management.
Architectural shifts include:
- Juniper’s AI-driven networks predict congestion before users notice delays
- AWS Wavelength pushes cloud capabilities to 5G edge devices
- Helium’s blockchain routers create decentralized area coverage
Sustainability gains momentum. Energy-efficient routing algorithms cut power use by 40% in trials. Ambient IoT will connect 30 billion sensors by 2030 without batteries. These trends showcase network evolution beyond traditional system designs.
As highlighted in our analysis of AI-driven networks, autonomous operations will become standard. The coming years promise seamless integration of terrestrial and orbital data highways.
Conclusion
Modern connectivity thrives on efficient systems that power businesses and daily life. From LAN setups to cloud architectures, each design serves unique needs while prioritizing security and performance.
Professionals can advance through certifications like CCNP or JNCIE. Continuous learning keeps pace with AI-driven management tools and evolving protocols. Sustainability challenges also push greener solutions.
Compliance standards ensure safe data handling across industries. Regular assessments help optimize existing infrastructures for future demands.
Start exploring how upgraded network solutions can transform your operations today. The right setup boosts productivity while keeping users protected in our connected world.
FAQ
What are the main components of a computer network?
The key elements include nodes (devices like computers, servers, and routers), links (wired or wireless connections), and communication protocols (rules for data transfer). Security measures like firewalls also play a critical role.
How does a LAN differ from a WAN?
A Local Area Network (LAN) covers a small area like an office, while a Wide Area Network (WAN) spans larger distances, often connecting multiple LANs. WANs use leased lines or the internet for data transmission.
Why are communication protocols important?
Protocols like TCP/IP and Ethernet standardize how devices exchange data. They ensure compatibility, speed, and reliability across different hardware and software systems.
What are common network security threats?
Risks include malware, unauthorized access, and data breaches. Solutions involve encryption, firewalls, and regular updates to patch vulnerabilities.
How do hybrid networks combine different technologies?
Hybrid setups merge on-premises infrastructure with cloud services, offering flexibility. For example, a business might use local servers for sensitive data while leveraging AWS for scalability.
What’s the role of routers and switches?
A: Routers direct traffic between networks, while switches manage data flow within a single network. Both optimize performance and reduce congestion.
Can networks function without the internet?
Yes. Isolated systems like intranets or storage area networks (SANs) operate independently, often for security or specialized tasks like high-speed data storage.
What future trends are shaping networking?
Innovations include 5G, edge computing, and AI-driven network management. These enhance speed, reduce latency, and automate troubleshooting.